Cyber attribution is the process of tracking and identifying the perpetrator of a cyberattack or other cyber operation. In an attribution investigation, security analysts attempt to understand the tactics, techniques and procedures (TTPs) the attackers used, and the “who” and “why” of the attack.
A complex undertaking, cyber attribution demands significant time and resources. Even then, there is no guarantee investigators will identify the perpetrator with reasonable certainly. If they do succeed, the organization might still refrain from making the findings public or pursuing legal action, depending on circumstances and the organization’s priorities.
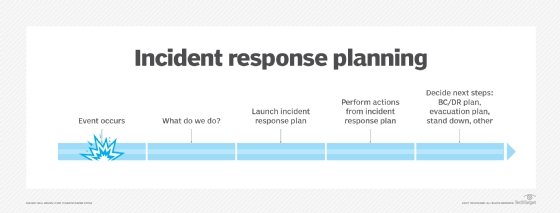
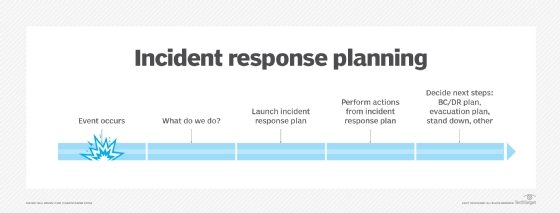
Cyberattacks can have serious consequences for businesses in terms of public relations, compliance, reputation and finances. After an attack, an organization will often launch an attribution investigation to get a more complete picture of the incident itself and to identify the threat actors.
An attribution investigation is sometimes part of an organization’s larger incident response plan. This approach can help an organization respond to a cyberattack more effectively while making it easier to launch the attribution effort. The investigation might also be conducted in conjunction with law enforcement agencies, cybersecurity firms or other organizations.
Cyber attribution is often viewed as a tool for reinforcing accountability and bringing cybercriminals to justice. It can also play an important role in protecting against future attacks. Security teams might better understand the TTPs cybercriminals used as well as their objectives and motivations. With such information, security teams can plan better defense and incident response strategies. The information can also yield insight into how best to prioritize their efforts and where to invest their resources.
Challenges of cyber attribution
Organizations often lack the resources or expertise needed to do their own cyber attribution, so they might hire outside security experts to assist in or carry out the investigation. However, cyber attribution can be challenging even for them.
To identify the threat actors responsible for a cyberattack, experts often conduct extensive forensic investigations. This includes analyzing digital evidence and historical data, establishing intent or motives, and understanding the circumstances that might have played a role in the attack. However, the internet’s underlying architecture provides threat actors with an ideal environment for covering their tracks, making it tough for investigators to track down the perpetrators.
Hackers typically do not carry out attacks from their own homes or places of business. Usually, they launch their attacks from computers or devices owned by other victims that the attacker has previously compromised. Hackers can also spoof their own Internet Protocol (IP) addresses or use other techniques, such as proxy servers or virtual private networks (VPNs), to confuse attempts at identification.
Additionally, jurisdictional limitations can hinder attribution investigations in cross-border efforts because investigators must go through official channels to request help. This can slow down the process of gathering evidence, which must occur as soon as possible. In addition, there is no international consensus about how to approach cyber attribution, nor are there any agreed-upon standards or principles.
In some cases, cyber attribution efforts are challenging when attacks originate in nations that refuse to cooperate with investigators in other countries. Such roadblocks can become increasingly problematic when political tensions are already high. Jurisdictional issues can affect the integrity of the evidence and chain of custody.
What does cyber attribution identify in an investigation?
Security experts use a variety of specialized techniques when performing cyber attribution. Although these techniques can be highly effective, producing definitive and accurate cyber attribution is quite difficult and sometimes nearly impossible. However, many organizations and governments still believe that attribution is worth the effort.
Cybercrime investigators use analysis tools, scripts and programs to uncover critical information about attacks. The investigators can often uncover information about the technologies used, such as the programming language, program’s compiler, compile time, and software libraries. They can also determine the order in which the attack events were executed.
Information of all types can prove useful to the attribution process. For example, if investigators can determine that a piece of malware was written on a specific keyboard layout, such as Chinese or Russian, that information can help narrow down the list of potential suspects.
During the attribution process, investigators also analyze any metadata connected to the attack. The metadata might include source IP addresses, email data, hosting platforms, domain names, domain name registration information or data from third-party sources.
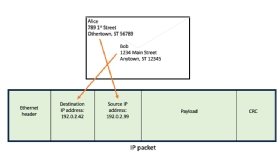
Metadata can help make a more convincing case for attribution. For instance, it might provide conclusive evidence that the systems used for the cyberattack communicated with nodes outside the targeted network. However, analysts have to be careful when relying on such data because data points can be faked easily.
In some cases, investigators will analyze metadata collected from attacks that have targeted different organizations. Doing so enables them to make assumptions and assertions based on the recurrence of falsified data. For example, analysts might be able to link an anonymous email address back to the attacker based on the domain names because they’re associated with a specific threat actor.
An important part of any attribution effort is to examine the TTPs used in an attack. Attackers often have their own distinctive, recognizable styles, and investigators can sometimes identify perpetrators based on their attack methods, such as social engineering tactics or type of malware, as those might have been used in prior attacks.
In addition, knowing what’s happening in related industries or certain organizations can help security experts predict attacks. For instance, companies in the natural gas industry spend more money on exploration when gas prices increase and, consequently, are at a higher risk for theft of geospatial data.
Understanding the attacker’s motives can also aid in cyber attribution. Security experts work to understand the perpetrators’ objectives, which might be related to financial gains, political advantages or other factors. Additionally, investigators try to discover how long the cybercriminals had been tracking the targeted systems, whether they were looking for specific data during their attack, and how they’ll try to use what they found.
Although cyber attribution isn’t an exact science, these attribution techniques can help cybercrime investigators identify the attackers beyond a reasonable doubt. The information can also be useful in protecting against future attacks.
Stopping cybercrime requires understanding how you are being attacked. Learn about the most damaging types of cyberattacks and what to do to prevent them. Also, check out our complete guide to incident response and improve your own cybersecurity implementation using these cybersecurity best practices and tips.


