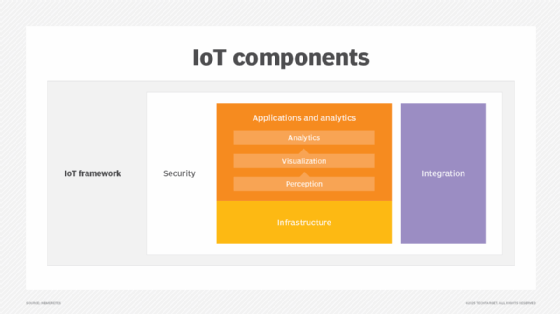
6 IoT architecture layers and components explained
Enterprise IoT continues to grow at a reported 20% annually, transforming operations across various industries, from manufacturing and logistics to healthcare and energy. As this expansion accelerates, enterprise IT and operational technology professionals must prepare to design, implement and manage increasingly complex IoT systems. The first step in achieving this is to determine the […]
Read MoreTop 15 IoT security threats and risks to prioritize
IoT endpoints are prime targets for attacks, with the soaring number of connected devices and often porous security controls creating plenty of opportunities for hackers. In its “The State of IoT Security, 2024” report, Forrester Research concluded that corporate IoT devices were the most reported target for external attacks, meaning they were attacked more than […]
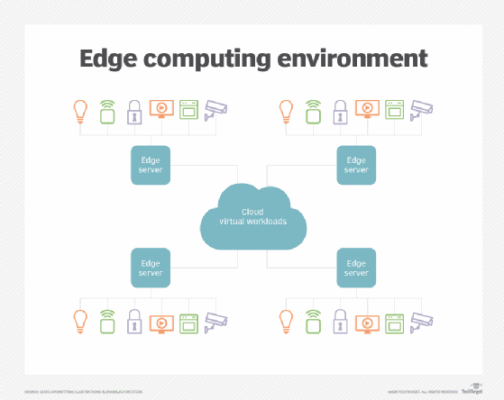
Read MorePrioritize security from the edge to the cloud
It can be tough to secure traditional cloud workloads. But workloads at the network edge face additional security challenges, such as a larger attack surface and elevated risk of physical security attacks. An effective edge-to-cloud security strategy mitigates threats across a business’s IT infrastructure while enabling efficiency and scalability in security operations. For businesses […]
Read MoreAI and IoT: How do the internet of things and AI work together?
IoT and AI are two of the hottest topics in tech, which is a good reason why enterprise technologists must understand them. The two technologies can be highly symbiotic, but the most significant opportunities might lie in using them together, so it’s critical to plan how they can support each other to benefit enterprise […]
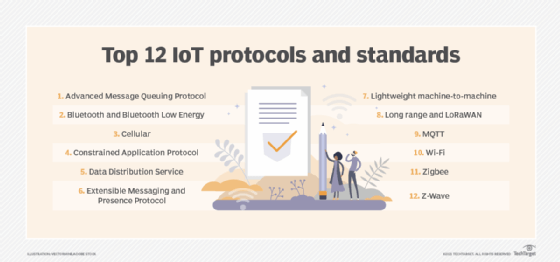
Read MoreTop 12 most commonly used IoT protocols and standards
There were 18.8 billion IoT connections in 2024, according to market research firm IoT Analytics. And researchers there estimated the number of IoT connections will swell to 41.1 billion by 2030. The availability and expansion of IoT protocols, along with 5G and low-power WANs, drive and support much of that growth. Why are IoT protocols […]
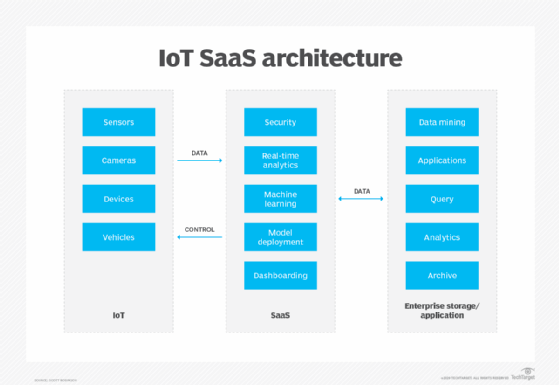
Read More6 IoT SaaS platform providers help streamline adoption
IoT devices are everywhere — from manufacturing to healthcare to wearables. Organizations use equipment or vehicles with IoT sensors to collect data and automate back-end processes to improve customer experiences and create new business models. But deploying these connected devices to get value from the data can be challenging. Providers are helping companies address […]
Read MoreWhat is IoT integration?
By Published: Jun 09, 2025 IoT integration is the process of linking smart devices, applications, databases and systems to facilitate data exchange and enable automated workflows. In manufacturing, integrating the internet of things (IoT) into operations can create a smart factory that automates routine tasks and optimizes operational performance and supply chain management. For example, […]
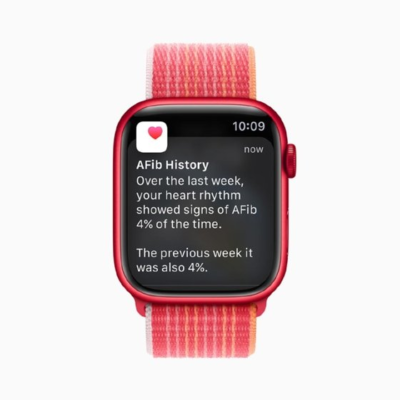
Read MoreApple watchOS (Apple Watch operating system)
What is Apple watchOS (Apple Watch operating system)? Apple watchOS is the operating system (OS) designed specifically for the Apple Watch wearable device, with features that take advantage of the smaller screen and location of the device on the user’s wrist. Apple watchOS is based on iOS, the operating system used for its iPhones and […]
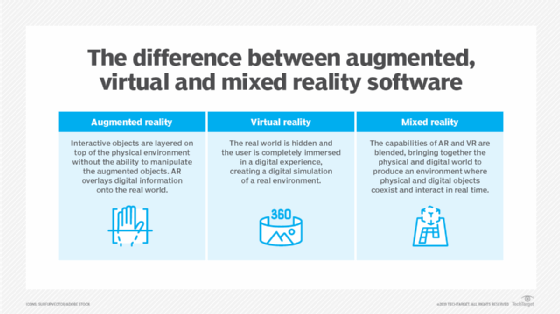
Read MoreWhat is VR locomotion (virtual reality locomotion)?
VR locomotion refers to the techniques and technologies that allow users to move within a virtual reality (VR) environment. Unlike real-world movement, where locomotion is intuitive and physical, moving through a digital space requires translation of user inputs — either physical or simulated — into virtual movement. As immersive VR continues to evolve, locomotion remains […]
Read MoreWhat is the OSI model? The 7 layers of OSI explained
The OSI model (Open Systems Interconnection model) is a multilayered reference model that shows how computer systems and applications communicate over a network. This seven-layer model provides a visual design of how each communications layer is built on top of the other, starting with the physical cabling, all the way to the application that’s trying […]
Read More