Databricks buys Tecton to give context to AI agents
IDC analyst and associate vice president Sharath Srinivasamurthy said that event-driven automation and analyzing data in motion is a critical enabler for enterprises desiring to scale their agentic systems. “When contextual, event-driven customer data and external signals are captured and analyzed in real time, the efficacy and responsiveness of AI agents significantly improves,” Srinivasamurthy said. Since event-driven agentic automation […]
Read MoreFrom cloud migration to cloud optimization
Control over infrastructure was mentioned by 41% of IT leaders. The argument for greater control is not new, but it has gained renewed relevance when paired with cost optimization strategies. Simply put, enterprises are asking tough questions about whether the public cloud meets all their operational needs. For an increasing number of organizations, the answer is no. […]
Read MoreMicrosoft adds MCP support to Visual Studio to boost development of agentic applications
“MCP acts like a secure ‘universal adapter’ for connecting AI agents (like Copilot) to external tools, databases, code search engines, or deployment pipelines, so there are no more one-off integrations for every service,” Walter said. “MCP helps connect to internal company tools securely, meaning that enterprise users can blend public AI advancements with proprietary processes […]
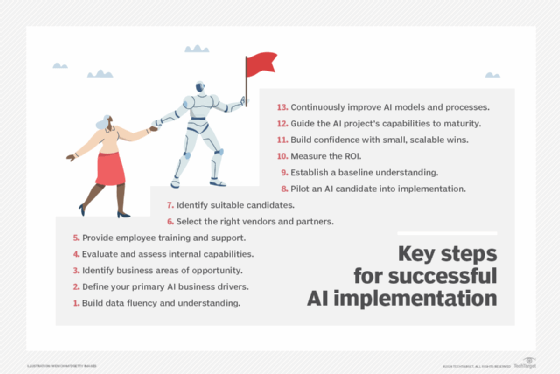
Read MoreAI implementation: 13 steps to achieve success in your business
AI technologies are quickly maturing as a viable means of enabling and supporting essential business functions. However, creating business value from artificial intelligence requires a thoughtful approach that balances people, processes and technology. AI takes many forms: machine learning, deep learning, predictive analytics, natural language processing, computer vision and automation. Companies must start with a […]
Read MoreGenerative AI dos, don’ts, and ‘undos’
AI agents are undeniably powerful, but wielding that power responsibly is another story. This month’s picks dive into the real-world dos and don’ts of generative AI: Best practices for using genAI tools for code generation, how to avoid the trap of over-relying on a single tool, and why so many agents fail at understanding business […]
Read MoreUp and running with Azure Linux 3.0
I first pulled the latest release from the Microsoft container repository and then had Podman run it as a named container, listing the file system contents to check that it was running correctly. I was then able to export the container contents from the image using the Podman export command, which creates a tarball from […]
Read MoreAWS blames bug for Kiro pricing glitch that drained developer limits
Pricing flip-flops and developer dissatisfaction In July, AWS had to limit the usage of Kiro, just days after announcing it in public preview, due to the sheer number of developers flocking to try out the IDE, mainly driven by pricing changes and throttling issues in rival IDEs, such as Cursor and Claude Code. It had […]
Read MoreIBM can’t afford an unreliable cloud
Opening the door for competitors IBM has traditionally been a niche player in the cloud market, holding a 2% global market share compared to AWS (30%), Microsoft Azure (21%), and Google Cloud (11%). IBM Cloud targets a specific enterprise audience with hybrid cloud integration and enterprise-grade features. AWS, Azure, and Google Cloud have consistently demonstrated […]
Read MoreGoogle adds VM monitoring to Database Center amid enterprise demand
This capability, according to Google, is a result of several enterprises demanding support for monitoring self-managed databases to gain full oversight of all their deployed databases. “This holistic visibility helps identify critical security vulnerabilities, improve security posture, and simplify compliance,” said Charlie Dai, VP and principal analyst at Forrester. These security vulnerabilities could include outdated […]
Read MoreMonitoring microservices: Best practices for robust systems
Logging. Implement a pre-defined logging with a well-known format (e.g., JSON). This ensures that logs from distinctive offerings are easily parsable and searchable, and provides quicker identification of issues. Include essential records like timestamps, provider names, log levels and unique request IDs. Distributed tracing. When a request flows via multiple services, distributed tracing presents a […]
Read More