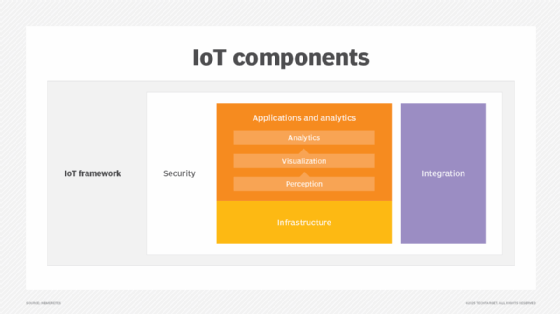
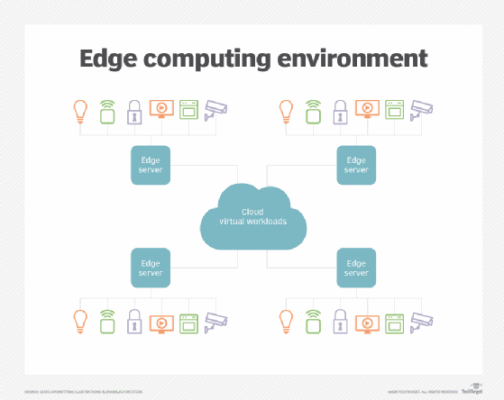
6 IoT architecture layers and components explained
Enterprise IoT continues to grow at a reported 20% annually, transforming operations across various industries, from manufacturing and logistics to healthcare and energy. As this expansion accelerates, enterprise IT and operational technology professionals must prepare to design, implement and manage increasingly complex IoT systems. The first step in achieving this is to determine the […]
Read MoreDeveloping JavaScript apps with AI agents
Matthew Tyson is a contributing writer at InfoWorld. A seasoned technology journalist and expert in enterprise software development, Matthew has written about programming, programming languages, language frameworks, application platforms, development tools, databases, cryptography, information security, cloud computing, and emerging technologies such as blockchain and machine learning for more than 15 years. His work has appeared […]
Read MoreTop 15 IoT security threats and risks to prioritize
IoT endpoints are prime targets for attacks, with the soaring number of connected devices and often porous security controls creating plenty of opportunities for hackers. In its “The State of IoT Security, 2024” report, Forrester Research concluded that corporate IoT devices were the most reported target for external attacks, meaning they were attacked more than […]
Read MoreRisk management in the public cloud is your job
I was excited to speak at a regional cloud computing summit hosted by one of the major cloud providers. My presentation focused on the many opportunities of public cloud and the essential need for risk management. Just before the event, I received an email stating that three of my slides, which discussed cloud outages and […]
Read MorePrioritize security from the edge to the cloud
It can be tough to secure traditional cloud workloads. But workloads at the network edge face additional security challenges, such as a larger attack surface and elevated risk of physical security attacks. An effective edge-to-cloud security strategy mitigates threats across a business’s IT infrastructure while enabling efficiency and scalability in security operations. For businesses […]
Read MoreHow to use editable installs for Python packages
When you install Python packages into a given instance of Python, the default behavior is for the package’s files to be copied into the target installation. But sometimes you don’t want to copy the files—sometimes, you want to link to them, so any installed version of the package can be updated by simply editing the […]
Read MoreGoogle touts Python client library for Data Commons
Google has released version 2 of its Python client library to query the Data Commons platform, which organizes the world’s publicly available statistical data. The library supports custom instances, among other capabilities. Announced June 26, the Data Commons Python library can be used to explore the Data Common knowledge graph and retrieve statistical data from […]
Read More